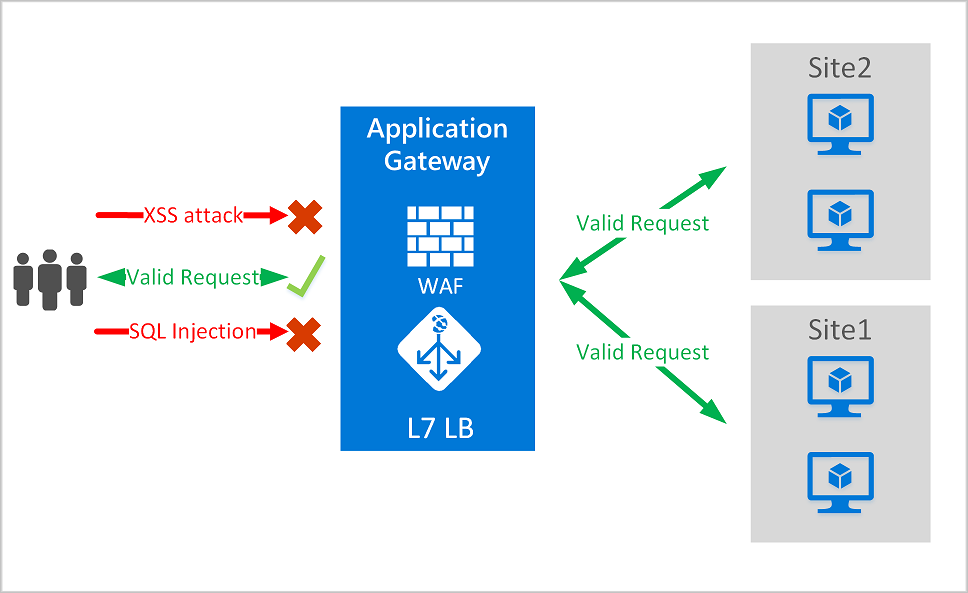
The Azure Web Application Firewall is one of the features of Azure Gateway and its main goal is to protect a web application to common exploits like SQL injections, cross-site scripting attacks and others, following the specifications of Open Web Application Security Project (OWASP, specifically the version 3.0 of Core Rule Set). IMHO, the best things of this service are the following:
- it works with any kind of web application (ASP.NET, PHP, JSP, etc..)
- it secures the application without doing any change to the code
- you can monitor the traffic using a set of specific logs and metrics, inside the Azure Gateway instance
In this post I would like to give a quick technical intro to Azure WAF, before going deeply into the steps for creating it via ARM. If you need a detailed description of what Azure WAF is and all its features, you can find everything inside the Microsoft documentation.
Azure WAF related resources
When you would like to deploy an instance of Azure WAF you must create also the following resources:
- Azure virtual network - This is the Azure resource needed for have the Application Gateway fully working. Inside this network you can only deploy other Application Gateway instances, without the possibility to have other types of resources.
- Azure public IP - This is the Azure resource that will give you the possibility to call WAF endpoints through internet. This resource will create a public IP address given by Microsoft.
Azure Application Gateway components, used by WAF
The service is based on the following components of Azure Application Gateway:
- Backend pools - The web applications that must be protected. These can be app services, IP addresses or hostnames, virtual machines that expose web apps through IIS or Azure Virtual Machine Scale Sets
- HTTP settings - Here you can specify how the Application Gateway must connect with the backend. For instance, you can specify the port for the connection or, if your web app is exposed via HTTPS, you can put the certificate for sending a valid request.
- Listeners - These are the first entry points for every HTTP or HTTPS call. If you have more than one listener in your instance, take a look at this page of the documentation for understanding the order in which they will be executed.
- Frontend IP configurations - The IP addresses that the listerners will use for receiving the calls. You can have public IP configurations or private ones.
- Rules - A rule define how a call received by a Listener is forwared to a backend pool. For instance, here you can specify a HTTP to HTTPS redirects.
WAF modes
A web application firewall can be configured in two ways:
- Detection - The service is working, but it does not block suspicious requests. It only logs them.
- Prevention - The seervice immediatly blocks suspicious requests.
WAF pricing
Azure web application firewall can be charged based on the version you choose during deployment:
- Web Application Firewall - Here you have the per-hour price of an Azure Application Gateway with a Medium size at least. In addition, there's the price based on the amount of data that the WAF will process.
- Web Application Firewall V2 (avialable from the 30 of April, 2019) - Here you have a specific per-hour price and a cost based on the amount of "Capacity units" that you will choose to have. Here a detailed explanation of what a capacity unit is.
Here you can find the differences between V1 and V2, in terms of features.
Important info to be aware of
There are few things that need your attention before starting to use the Azure Application Gateway features in your architectures:
- You can deploy a maximum of 1000 instances of Application Gateway for each subscription
- The maximum number of HTTP listeners for one single instance of Application Gateway is 100 listeners. Related to this, you have to remember that a simple HTTP to HTTPS redirect need you to have two different listeners deployed.
- The maximum size of certificates is 10 KB for V1 SKU and 16 KB for V2 SKU.
- If your application gives the possibility to final users to upload files, there's a maximum upload size to respect: 100 MB for WAF in Medium size, 500 MB for WAF in Large size.
You can find here all the other limitations of the service.